Managed Cyber Security
Stay Ahead of Threats: Take Control of Your Security Before It’s Too Late.
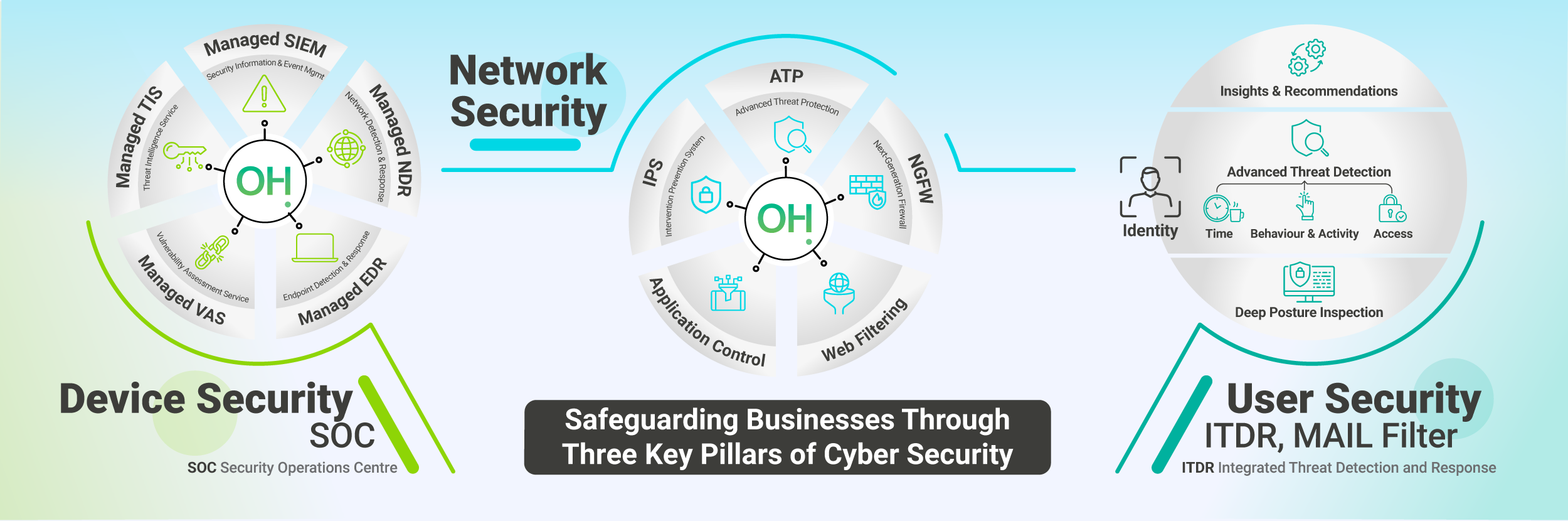
Device Security
Proactively protect your endpoints—laptops, mobiles, servers, and IoT devices—through tailored assessments that assess vulnerabilities, enforce device control policies, deploy encryption and patch management, and integrate advanced endpoint protection and detection. Enjoy proactive MDR-backed monitoring, compliance mapping, and remediation so you can stay resilient—and compliant—across your device estate.
Network Security
Safeguard your network from evolving cyber threats with layered protection. From firewalls, intrusion prevention, and secure VPNs to cloud security, segmentation, and Zero Trust access, we protect every connection point. Intertwined with the device 24/7 SOC monitoring and EDR services, we keep your network resilient, compliant, and ready for the future.
User Security
Strengthen your first line of defence—your people. We protect users through strong identity and access controls, multi-factor authentication, role-based permissions, and proactive monitoring. Combined with awareness training and phishing simulations, we reduce human risk, stop credential-based attacks, and keep your organisation compliant.
Endpoint Detection and Response
Managed EDR goes beyond traditional antivirus, detecting and stopping sophisticated threats before they impact your business.
Updating & 3rd Party Patching
Reduce risk and downtime with proactive patching across Windows, macOS, and third-party apps like browsers, Java, and Adobe.
Security Operations Center (SOC)
Around-the-clock monitoring and threat hunting from our SOC team, ensuring rapid detection, response, and remediation.
Security Information and Event Management (SIEM)
Gain full visibility across devices, networks, and users with real-time log monitoring, threat correlation, and compliance-ready reporting.
Enhanced Encryption
Safeguard confidential information and meet compliance requirements by encrypting data at rest and in transit—protecting it against loss, theft, or breach.
Data Security
Backup & recovery
Data Loss Prevention (DLP)
Ransomware resilience
Protecting data-at-rest & in-transit
Firewalls, IDS/IPS
Strengthen your network security and compliance posture with advanced firewalls and real-time intrusion detection and prevention.
Web Filtering
Web filtering protects your users from malicious sites, blocks unsafe content, and enforces policies—no matter where they’re working.
VPNs & Scure Remote Access
Provide secure, compliant access to your network and cloud services, reducing risk from unsecured connections.
Application Control
Application control ensures only approved software runs on your devices, blocking risky apps and reducing security threats.
Cloud & Application Security
SaaS security (Microsoft 365, Google Workspace)
Cloud workload protection (Azure, AWS)
Application vulnerability management
CASB (Cloud Access Security Broker)
AI Powered Mail Filtering
AI-powered email filtering stops sophisticated phishing and malware that standard filters often miss, keeping your inbox—and your business safe.
Identity Threat Detection and Response
Identity Threat Detection and Response stops account takeovers and insider threats that traditional security tools can’t see, keeping your users and data safe.
Accountable Access Control
Enforce role-based access, track user actions, and demonstrate accountability for compliance and security audits.
Phishing simulations & awareness training
Manage access confidently with complete visibility and accountability.
Governance, Risk & Compliance
Manage access confidently with complete visibility and accountability.

Take Control of Your Cyber Security
Stay Ahead of Threats: Take Control of Your Security Before It’s Too Late.
Benefit from OhTech’s In-House Security Expertise: Audits, Remediation, and Ongoing Protection.
Comprehensive Security Reviews and Penetration Testing
As your partner, OhTech provides comprehensive point-in-time audits that enable us to identify and mitigate risks, ensuring a more secure business environment.
Phishing Awareness
Empower employees to deal with modern-day phishing attacks through regular phishing awareness testing and training — using an education-first approach to reduce the risk from the prevalent threat.
Dark Web Scanning
Review the company information available for purchase on the dark web, including personally identifiable information (PII) and leaked credentials that’ve been stolen and cannot be controlled.
Cyber Essentials
Manage infrastructure audits, certification guidance and required remediations for Cyber Essentials and Cyber Essentials PLUS with OhTech as the awarding body.
PenTesting
Test the security controls of your systems, networks and infrastructure through a penetration test to safeguard against external threats.
IR Readiness Assessment
Ensure your teams/provider have a comprehensive Incident Response plan that is easily available to all responders in the event of a breach.
CyberSCAN
Scour for potential threats inside your internal and external networks with our managed vulnerability scanning solution.
GAP Assessments
Gain a detailed analysis of your cyber defences through GAP assessments that align with industry standards (CE, NCSC, ISO 27001, CIS, NIST) and a clear roadmap for improving compliance, evolving security and remediating vulnerabilities.
Infrastructure Assessment
Establish whether attackers can compromise assets like customer or financial data within your business-critical systems.
Application Assessment
Conduct automated and manual penetration tests to assess the security of specific applications and/or code structures.
Web App Assessment
Identify vulnerabilities in business applications accessed via standard web interfaces, whether internally or externally.
Wi-Fi Assessment
Highlight gaps such as unsecured encryption protocols, misconfigurations and weak access controls in your Wi-Fi networks.
Firewall Assessment
Check the configuration of your firewall devices to identify weaknesses or incorrect and sub-optimal setups.
Require Cyber Essentials or Cyber Essentials PLUS?
At Oh-Tech, our goal is to help every business we work with achieve the recognised standard of Cyber Essentials.
We provide both levels of accreditation, tailored to your organisation’s needs.
Discover how Cyber Essentials can strengthen your business by visiting our dedicated page.

Cyber Essentials is an online self-assessment questionnaire that assesses your business’ level of cyber security.

Cyber Essentials PLUS includes the online self-assessment as well as an audit of your IT systems to ensure your compliance — completed by our in-house cyber experts and partners.
Concerned about your business's cyber protection?.
That's why we make it easy — simply request a convenient cyber audit!
Heres the deal...
Quick and convenient
Our customised audit takes minutes to set up and requires minimal time from you.
Expert insights
We audit your IT infrastructure, security, managed IT support and services, along with your policies and procedures. We highlight the business impact of any areas of concern.
Audit report
This is delivered alongside our expert insights and includes a simple ‘RAG’ review, showing clearly where your IT infrastructure is strong, vulnerable or weak, with supporting detail. (see diagram to the right).
Easy to Switch
If we find that there are vulnerabilities and weaknesses in your IT, we outline how Oh-Tech can benefit you, which usually includes making financial savings. We make it as easy as possible for you to outsource to us. There is of course no obligation to do so.

Get in touch today and see how we can support your businesses IT
To find out more on how Oh-Tech can help your business, complete the form and a member of our team will be in touch.
Alternatively you can call us directly to speak to one of our experts. We look forward to hearing from you.